Introduction: The Need for Data Security
In today’s digital age, data security has become increasingly vital. As we rely more on technology, personal information and sensitive data are stored on hard drives, making them potential targets for data breaches. Whether you are upgrading your computer or disposing of your old hard drive, knowing how to destroy a hard drive safely is essential. This guide explores various methods that can help you protect your data from unauthorized access.
Why Destroying Your Hard Drive Matters
Data Breaches and Their Consequences
How to destroy a hard drive? Data breaches can lead to serious consequences, including identity theft and financial loss.
Personal Information Risks
- Identity Theft: One of the most significant repercussions of inadequate data protection is identity theft.
- This occurs when unauthorized individuals gain access to personal information and use it for fraudulent purposes.
- Compromised Sensitive Data: Key pieces of information, such as:
- Name: Your full name can be used to impersonate you.
- Social Security Number (SSN): This unique identifier can exploit to open new accounts, take out loans, or obtain official documents in your name.
- Financial Records: Access to bank account details, credit card numbers, and other financial information can result in unauthorized transactions and significant financial loss.
- Emotional and Psychological Impact: Victims of identity theft may experience stress, anxiety, and a long recovery process to restore their identity.
- Long-term Consequences: Recovery from identity theft can take years, affecting credit scores and personal finances.
Business Liability
- Increased Stakes for Organizations: The implications of a data breach are far graver for businesses compared to individuals.
- Legal Repercussions:
- Companies can face lawsuits from affected customers, which can lead to significant legal costs and settlements.
- Regulatory fines may also be imposed for failing to comply with data protection laws.
- Loss of Customer Trust:
- A data breach can severely damage a company’s reputation, leading to a loss of customer loyalty and trust.
- Potential customers may choose to engage with competitors instead, resulting in a decrease in sales and market share.
- Financial Liability:
- Businesses may incur direct costs, such as investigation expenses, notification costs, and remedial measures to secure systems.
- Additionally, long-term financial impacts could ensue from lost revenue and increased insurance premiums.
- Operational Disruptions:
- A data breach can divert attention and resources away from core business functions, leading to operational inefficiencies.
Legal Implications
In some cases, businesses are legally obligated to protect consumer data. Failing to do so can result in legal penalties and fines. Understanding the importance of hard drive destruction is essential to mitigate risks not only for individuals but also for organizations.
Safe Methods to Destroy a Hard Drive
Method 1: Data Wiping Software
How to destroy a hard drive? One of the most efficient ways to destroy data on a hard drive is by using specialized data-wiping software.
- Select Trusted Software: Programs like DBAN (Darik’s Boot and Nuke) or Eraser can help in securely erasing data. They use algorithms that overwrite existing data multiple times.
- Step-by-Step Process: To use data-wiping software:
- Download and install the software on your computer.
- Connect the hard drive you wish to wipe (external or internal).
- Follow the software prompts to perform a secure wipe.
- Verification: After wiping, verify that the data has been completely erased by attempting to access files. You should find that no recognizable data remains.
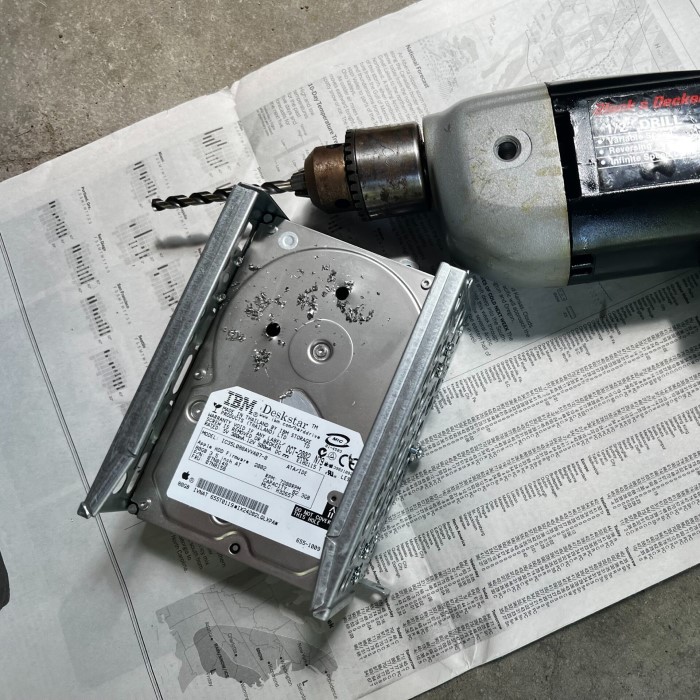
Method 2: Physical Destruction
If you want to ensure your hard drive cannot be recovered, physical destruction is an effective option.
- Tools Required: You may need a hammer, drill, or hard drive shredder for this method.
- Steps for Physical Destruction:
- Power Down the Device: Before starting, power down the computer and unplug it.
- Remove the Hard Drive: Carefully remove the hard drive from your device.
- Destroy the Drive:
- Hammer: Use a hammer to break apart the hard drive. Target the circuit board and platters.
- Drill: Drill holes through the drive to damage the internal components.
- Shredder: If available, use a hard drive shredder for complete destruction.
- Safety Precautions: Always wear protective gear like safety goggles and gloves when physically destroying a hard drive to prevent injury.
Method 3: Degaussing
Degaussing is another method used primarily for older magnetic drives.
- What is Degaussing?: This process uses a degausser, a device that generates a powerful magnetic field to disrupt the magnetic properties of the hard drive, effectively erasing all data.
- How to Degauss a Hard Drive:
- Obtain a degausser that is compatible with your hard drive.
- Follow the manufacturer’s instructions on how to use the degausser for effective data erasure.
- Limitations: Be aware that degaussing may not be effective against solid-state drives (SSDs) since they do not store data magnetically.
Steps to Dispose of a Destroyed Hard Drive
Proper Disposal Methods
After securely destroying your hard drive, consider how to dispose of it properly.
- E-Waste Recycling: Many communities offer electronic waste recycling programs. Look for local facilities that accept electronic waste.
- Donation Services: Some organizations accept broken parts for educational or technical training purposes.
Environmental Considerations
- Avoid Landfills: Never just throw hard drives in the trash. They contain hazardous materials that can be harmful to the environment.
- Choose Eco-friendly Options: Find recycling programs that follow best practices for handling e-waste while minimizing environmental damage.
Troubleshooting Hard Drive Destruction
Issues with Software Wiping
Insufficient Program Features:
Limitations of Software: Some data-wiping software may lack comprehensive features that ensure all files and data securely erase. This can lead to sensitive information remaining retrievable.
Verification of Process: If you suspect that the software hasn’t effectively wiped all data, it’s crucial to double-check that you have followed the correct procedure during the wiping process.
Exploring Alternatives: In cases where the current software fails to meet your data-erasure needs, consider researching and using alternative software options that offer more robust features for data wiping.
Drive Corruption:
Risks with Older Drives: Older storage devices can often suffer from corruption issues, which can hinder the ability of data-wiping software to complete a full and secure wipe of the drive contents.
Overall Recommendations:
Backup Important Data: Always perform backups of important files before attempting any data wipe, especially if you suspect your drive may be at risk of corruption.
Consult Professionals: If uncertain about the adequacy of your data-wiping methods or the condition of the drive, it may be beneficial to seek advice from IT professionals who specialize in data security.
Physical Destruction Challenges
Safety Considerations:
When engaging in the physical destruction of hard drives, it is crucial to prioritize safety.
Use protective gear such as gloves, goggles, and masks to prevent injury from flying debris or sharp objects.
Be aware of your surroundings and ensure that the area is secure to avoid any accidents.
Seeking Professional Help:
If you feel uncertain or lack the proper tools and knowledge for safe hard drive destruction, it is advisable to consult with professionals.
Companies that specialize in hard drive destruction services equip with the necessary expertise and equipment.
Utilizing professionals not only ensures safety but also guarantees compliance with data protection regulations.
Ensuring Complete Damage:
It is essential that, during the physical destruction process, the internal components of the hard drive—specifically the platters and circuit boards—are completely destroyed.
The damage should be thorough enough to render data recovery impossible, which often involves methods such as shredding or crushing the hard drive.
Confirm that there are no intact parts that could potentially allow for the recovery of sensitive information, thereby safeguarding against data breaches.
Final Verification:
After destruction, inspect the remnants of the hard drive to ensure that it has been effectively compromised.
Consider documenting the destruction process, possibly through photos or certificates, especially if this is for business or compliance purposes.
Regularly review and update your data destruction policies to remain in line with best practices and evolving security standards.
Frequently Asked Questions (FAQs)
How do I destroy data on my hard drive?
You can destroy data by using specialized software, physically destroying the drive, or degaussing to disrupt magnetic data storage.
Is data permanently erased with software wiping?
Using data-wiping software correctly can make recovery highly unlikely, but physical destruction is the only way to ensure total irrecoverability.
Can I recycle my hard drive after destruction?
Yes, after properly destroying the hard drive, recycle it through e-waste programs rather than disposing of it in the trash.
What tools do I need for physical destruction?
Common tools include a hammer, drill, and specialized hard drive shredders. Always wear protective gear when using these tools.
Conclusion: The Importance of Secure Hard Drive Destruction
In today’s information age, understanding how to destroy a hard drive properly is crucial for data security. By employing safe and effective methods, such as data wiping software and physical destruction, you can protect your sensitive information from falling into the wrong hands. Always remember to dispose of destroyed hard drives responsibly to minimize environmental impact. Whether you are a business owner seeking to comply with data protection laws or an individual looking to safeguard personal information, using these strategies ensures that your data remains secure long after its digital life has ended. Prioritize your data security, and make informed choices about hard drive destruction!